Cryptography: Caesar, Enigma and the Blockchain
February 1, 2022
6 min

Cryptography is a key component of the blockchain, but it is also used to protect our online browsing or our messages with friends.
We can only fully understand the genius of the blockchain by understanding what cryptography is.
The ancient origins of cryptography
Cryptography has a very ancient history, so much so that the first evidence of its use dates back to 1900 BC in an Egyptian tomb, in the form of hieroglyphics.This mystical context is entirely appropriate for the first appearance of cryptography, a term derived from the Greek words for “secret writing“.
The purpose of cryptography has always been to enable communication in the presence of people who were not supposed to understand the message. Consequently, its use has mainly marked the history of warfare.The first cryptographic technique that is still relevant today is the one used by Julius Caesar for military purposes, the so-called “Cesar Cypher“.Caesar used a 3-key: he replaced each letter of the message with the third one that followed it (e.g. F instead of C).Thanks to modern technology, this system has now fallen into disuse, but it was used for a long time.
Orthodox Jews, for example, used Caesar’s cipher to encrypt the names of God on the back of the mezuzah when it was forbidden to write or pronounce his name.The mezuzah is a roll of parchment attached to the doorposts of houses, where passages of the Torah are written.
Another classic model of encryption is permutation, which involves distributing the message in a table and reading the table in another direction to create the final encrypted message.
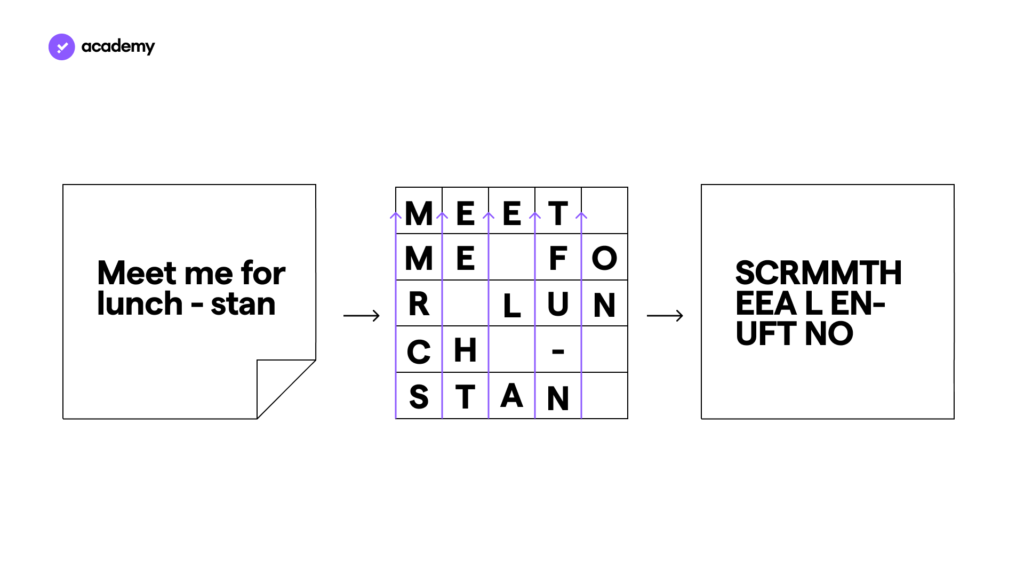
Cryptography then evolved into more complex systems, leading to solutions such as Enigma, the famous device used to encrypt messages during World War II.
Enigma: the genius of Alan Turing
Enigma is the turning point in the history of cryptography. Enigma was first cracked by the Polish government before the German invasion, using an electromechanical machine.The problem, however, was that the Germans kept making the Enigma mechanism more and more complex.
The Englishman Alan Turing succeeded in automating the calculation to decrypt all versions of Enigma, allowing the Allies to defeat the Rome-Berlin Axis on several occasions.Among his many contributions, after the war Turing designed one of the first computer models, and gave the idea for what would become the Turing test.
How did Enigma work?
Enigma followed the same basic principle as Caesar’s cipher, namely the substitution of letters for other letters according to a criterion.
The difference is that Enigma makes this criterion much more complex.
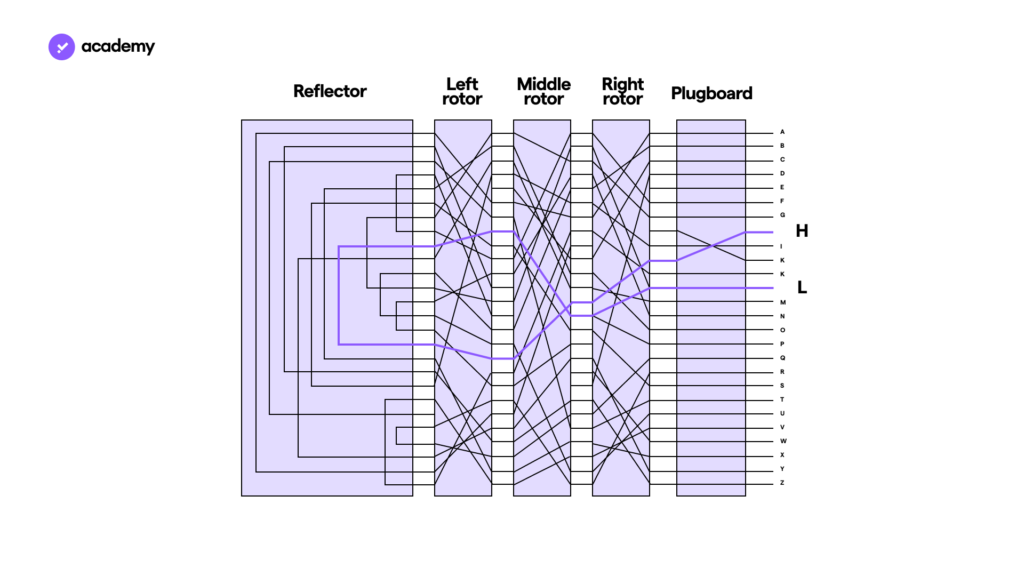
The device looked like a typewriter, but behind the keyboard it had 3 rotors with bundles of letters on them and at the bottom a reflector that sent back the electrical signal.
Each rotor had cables running through it that crossed different pairs of letters, while the diagram on the right makes the correspondence between the letters clearer.
Encryption worked like this:
- Pressing a letter on the keyboard sent an electrical input.
- The cable attached to the letter crossed 3 pairs of letters on the 3 rotors
- came back through the same rotors, but through different combinations of letters.
In the image below is an example of an input, the letter H, which returned the letter L as an output.
Cryptography in the age of the Internet
The arrival of computers marked a momentous step for cryptography and data security.Cryptographic algorithms are no longer based on machines, but on software. One of the first software packages to be released was the Data Encryption Standard, created by IBM in 1977, which included 64-bit long keys that could only be decrypted by the means available to the US security agency.With the evolution of computers, in 1999 this standard became decryptable even for large companies, thus making it obsolete.
In 2001, the Advanced Encryption Standard was thus drafted, with longer cryptographic keys, and with a more complex algorithm, involving both substitution and permutation, in an advanced mix of processes repeated more than 10 times.AES is still used today for WiFi connections and to connect to websites.
All the techniques we have discussed so far are based on symmetric encryption.This means that the key to decrypt the message is known to both the sender and the recipient, and is the same.There is a more secure option, which makes it even more complex for third parties to decrypt a message: asymmetric key cryptography.
Blockchain cryptography
One of the most secure forms of cryptography is that used by the blockchain, namely asymmetric key cryptography.This model is unidirectional and relies on two keys: a private key and a public key.While the public key allows the sender to encrypt the data, the private key allows the recipient to decrypt it.It is unidirectional because from the private key the public key can be obtained, but from the public key the private key cannot be deduced.Furthermore, only the recipient has the private key.
This type of encryption is also used by secure sites. When you connect to a site and see a padlock icon, it means that your browser has used public key cryptography to verify the site’s server, has established a temporary secret key with it and has used symmetric cryptography to protect all subsequent data exchange.
In the blockchain, this key pair is primarily used to secure the custody of cryptocurrencies. To use cryptocurrency wallets you need a private key, with which you decrypt the contents of your wallet and which also acts as a signature to confirm transactions or settings.
The public key, on the other hand, can be communicated and is used to send cryptocurrencies, or have cryptocurrencies sent to you. Find out more in the article on wallet keys.


