Cryptography and the Blockchain Technology
June 25, 2020
7 min

Introduction
On a structural level, the Blockchain is a growing list of records, called blocks, which are interlocked by encryption. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data.
Nakamoto didn’t create the blockchain out of nothing, he improved formulations by Stuart Haber and W. Scott Stornetta from 1991 about a cryptographically protected “chain of blocks” system to store documents. To this, he combined the discoveries of the computer scientist and cryptographer Hal Finney (2004), who introduced a system called RPoW, Reusable Proof Of Work, which will be decisive for the history of cryptocurrency. The great merit of Satoshi compared to his predecessors was to be able to give concrete applicability to the blockchain technology with Bitcoin.
A Chain of Blocks
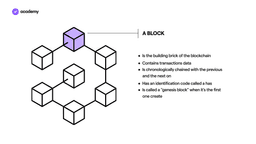
The blocks literally form the structure of the blockchain. These blocks are arranged in a linear sequence that forms an infinite chain. We can imagine the blocks as a sort of digital record where thousands of invoices and receipts are stored.
Each record, i.e. each block, records the data of a transaction such as, for example, the time, date, amount and who participated in the exchange. The blocks are linked to each other in chronological order and have a specific identifier that distinguishes them from all the others, called hash.
Each block can account for a certain number of transactions. Once its storage space is finished, a new block is created and concatenated with the previous one. Going back, we can find the first created block of a blockchain: the genesis block.
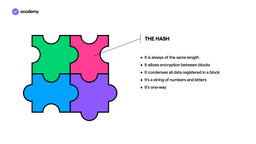
The hash is the glue that holds the blocks together. Hashing is used to link and condense groups of transactions into blocks, as well as to produce cryptographic links between each block, thus effectively creating a blockchain.
When combined with encryption, hashing algorithms can be very versatile, offering security and authentication in a variety of ways. In a sense, hashing is what gives each block a unique identity. If we imagine a block as a piece of a puzzle, the hash is what defines its shape, so that it can only be attached to the previous and next block chronologically.
Safety and Immutability: the Hash
All blocks within the blockchain are connected to each other, so tampering with a single block requires tampering with all its connected blocks. Not only is this difficult, but there are other protections that the blockchain provides. Personal digital signatures – known as private keys – are another security measure to ensure that digital assets are not misappropriated. To successfully attack a blockchain, at least 51% of the network should be controlled by an attacker at the same time. Since this is almost impossible, the blockchain is much more secure than existing payment systems.
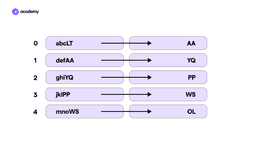
As we can see, blockchain security starts with blocks and hashes. To understand its mechanics, let’s try drawing two columns on a sheet. Each box in the first column represents a block and the transaction data saved in it. The second column contains the corresponding hash of each block.
When block 0 has used up its storage space, the saved data is converted into a two-letter identifier – AA – which will be used as part of the next input. The same with block 1, which will convert the data to the YQ hash.
For example, if someone tried to delete a transaction recorded in block 1, the alteration would change the combination of the letters in the block, then the hash and with a domino effect it would have to change all the subsequent and previous blocks. Even if we wanted to change the last block, it would be almost impossible. According to the mechanics we have just seen, the OL hash is the product of all the previous combinations. Changing it would visibly alter the whole blockchain.
The two-letter identifier in the second column is a simplification to show how a hash works. Now let’s see what it is in detail.
The hashing consists of taking the block data (input), passing it through a mathematical function and transforming it into a hash (output) of the same length. When the input varies even by a small detail, the output immediately changes. The fact that you can never get the same output from two different inputs (so there is no collision) is a strong security element, which is why if you try to tamper with a block, you inadvertently generate a change throughout the blockchain.
The hash function is also applied to each recorded transaction. Within a block each transaction generates a hash that also contains the hash of the previous transaction.
In addition, the hash function is designed to be unidirectional (one-way), a function that is difficult to reverse: the only way to recreate input data from the output of a hash function is by trial and error, trying to associate all possible combinations. We are talking about billions and billions of attempts, practically unsolvable even by the computer with the most advanced and powerful computing ability.
This is why it is said that once recorded, a transaction on the blockchain cannot be modified or deleted. Transactions are therefore irreversible, which means that even in the unlikely event of a network being successfully hacked, existing transactions can never be undone.
This ability of the blockchain to prevent alteration of already confirmed transactions means that it is defined as unchangeable. As we will see, immutability, combined with consensus algorithms, provides the network blockchain’s data security structure. Put simply, while the consensus algorithms ensure that the rules of the system are respected, immutability ensures data integrity.
Conclusion
What we’ve seen are just the first building blocks that make the blockchain so secure and different from traditional archiving methods. We can understand now what revolution Satoshi Nakamoto brought when he used it to create a payment system with Bitcoin.
Unlike the payments we make on a daily basis, blockchain payments are not handled by a central authority such as a bank or government. In fact, to make a blockchain payment, you do not need to have a bank account, or live in a free and democratic country or provide any kind of guarantee. Anyone with an internet connection can use the blockchain to make payments in cryptocurrency. In the next chapter, we will come to understand what it means to move value without the authorisation of a central authority.