Security Tokens and Security Token Offerings: What are they?
October 14, 2021
6 min

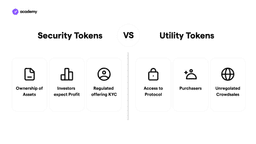
Security tokens are cryptocurrencies, usually based on the Ethereum blockchain, that represent the dividends of the company issuing them. Unlike utility tokens, they must be approved by regulators through lengthy bureaucratic procedures.
What is a Security?
Some financial instruments in certain jurisdictions may not be called securities, but in the US the term refers to these asset classes:
- Equity securities
- Debt securities (such as bonds)
- Derivatives (such as futures)
Security token and tokenised token: differences
First of all, a distinction must be made between two terms that are often confused: tokenised security and security token.
They are both digital assets that must be regulated, but the different order of the words “security” and “token” already reveals the difference between the two terms.
Tokenised securities are first and foremost securities, i.e. regular shares of a company. These securities are later issued in the form of blockchain-compatible tokens.
Security tokens, on the other hand, are originally native tokens of a blockchain, which inherently have a security function instead of, say, a utility or governance function.
Being native to the blockchain, security tokens are also programmable, as their protocol can be designed to support technologies such as smart contracts.
The regulation of such a complex asset is virtually uncharted territory, so the process to be able to deploy them in the market is not yet standardised and faces many obstacles.
Security Token Offerings (STO)
STOs are Security Token Offerings, i.e. the initial public offering of tokens representing a security.
The STO formula is derived from a combination of IPOs and ICOs.
IPOs are typical of traditional finance, as they consist of a public offering of shares in a public company to institutional or private investors.
Usually a bank underwrites the IPO and then lists the shares on one or more stock exchanges.
Through the IPO, a private company goes public and raises equity to scale up.
The ICO is the equivalent for cryptocurrencies. The main difference is that ICOs are not regulated by any institution, but take place directly on the blockchain without the need to verify the identity of investors through the KYC procedure.
Most of the utility tokens born between 2013 and 2017 were launched with an ICO, among them for example Ethereum and Ripple.
STOs, on the other hand, combine these two worlds, offering the possibility to buy shares in blockchain projects.
What problems are STOs encountering?
Because they have to be regulated sales of regulated tokens, STOs require a lot of time and costs to get all the papers in order through lengthy legal procedures, often not even well defined.
Three factors are limiting the potential of STOs and security tokens in general: regulatory uncertainty, the absence of dedicated bodies or services, and low liquidity.
Without defined regulations, however, there can be neither infrastructure nor liquidity. It is therefore clear where to start.
The regulators’ perspective
The SEC (Securities Exchange Commission) in the US is just an example of the countless regulators around the world who are issuing new statements and changing members and executives every day, all the while trying to understand and regulate blockchain technology and cryptocurrencies.
The SEC has already registered some STOs between 2020 and 2021, including that of Exodus.
These tokens in fact seem to be an excellent meeting point between the two worlds: at last the financial authorities have found a cryptocurrency that allows to be regulated.
Of course, this also means big steps backwards on the spectrum of decentralisation.
Ethereum Standards for Security Tokens
Turning to the more technical side of things, Ethereum developed a token standard library specifically for security tokens in 2021.
In fact, ERC-1400 makes it possible to regulate the exchange and holding of a token according to the needs of an STO and a regulated token.
This is possible thanks to all the individual standards that the ERC-1400 contains:
- ERC-1594 – Core Security Token
Supporting off-chain data integration to facilitate regulation and seamless interaction with the world outside the blockchain.
- ERC-1410 – Partially Fungible Token
While normally only the balance of a wallet can be seen on explorers, this standard also makes readable data such as STO-required vesting times, voting privileges and the provenience of tokens. The standard can also regulate when the token is fungible and when it is not, such as within specific dapps.
This information is important to verify token distribution and governance enforcement.
- ERC-1643 – Document Management
The standard allows notarial documents to be attached to tokens, also notifying the owners of any updates to the documents.
Documents can also be registered on the blockchain to ensure immutability.
- ERC-1644 – Controller Token Operation
Allows the regulator to force a transfer between two wallets if necessary, e.g. in circumstances of fraud or lost private keys.
- ERC – 2258 Custodial Ownership Standard
This standard addresses the need for security tokens to cover a more complex concept of ownership. Security tokens can be held in custody either directly by their owner (custodial owner) or by an entity on behalf of the token owner (beneficiary owner).
Ethereum is not the only blockchain to fully support these tokens: the Polymesh blockchain, with its Polymath token, is a project that immediately adopted this library of standards by applying it to its standard ‘ST’ format. Polymesh is a purpose-built blockchain to host security tokens from any project and also supports Dapps.
As always, however, it is Ethereum that has been driving innovations since the days of ICOs, thanks to its extensive programmability. It is on its test network that private and institutional developers test new standard tokens, scalability solutions and unseen protocols.