Social Engineering: the psychology of crypto scams
August 22, 2023
10 min

Online scammers are unfortunately often commonplace. They use manipulation mechanisms to induce their victims to reveal sensitive information (such as passwords), or to obtain money, sometimes in the form of cryptocurrencies. Since these deceptive scams are based on psychological vulnerabilities which could affect any of us, it is important to recognise them and to know the tools to be able to deal with them. Let’s find out what these deceptive strategies, known as social engineering, are and how we can protect ourselves.
What is Social Engineering?
A fundamental parameter of any computer system is security. Beyond performance, all technology must be protected from malicious attackers: so-called hackers or sometimes scammers. In relation to blockchain technology, we already know that exchanges of cryptocurrencies are secured by public and private key cryptography. Both of these keys are saved in your personal wallet. They are alphanumeric strings, so complex that they are almost impossible to guess. However, scammers could exploit mechanisms that are in a sense not as sophisticated as cracking these codes.
If hackers are identified by their use of programming and codes, scammers act on a ‘human‘ level. They do not exploit vulnerabilities in software, but in people. In other words, they condition users to share valuable data, such as access to their accounts or other secret codes. They do this through manipulation strategies, summarised by the term “Social Engineering”.
Scammers usually lure a certain pool of users by contacting them directly and en masse, either by exploiting social networks or by abusively infiltrating online communities. In order to better understand what social engineering is and to recognise the possible threats you may come across, it is important to understand how scammers act before and after contacting you.
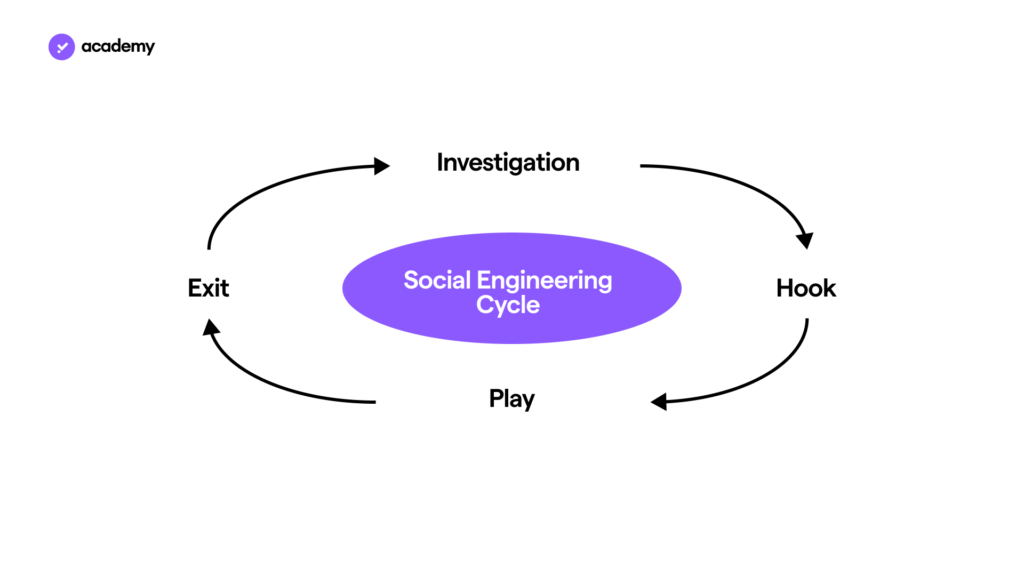
The process of Social Engineering involves a kind of vicious circle, marked by four steps:
- Investigation: after identifying the target, the scammer gathers as much useful information about him/her as possible. The background, constructed in this manner, makes it possible to define the profile and personal context of the victim. This is done with the goal of discovering his or her weak points. Based on these, the approach is planned, choosing the most suitable social engineering strategy.
- Hook/contact: the investigation period culminates in the first interaction with the target user. Thanks to the information gathered, the scammer tries to create a climate of trust and thus convinces the victim to communicate. This is a crucial phase because if the victim avoids contact, it could save him/her from the scam. The longer that contact is avoided, the easier it will be to escape the manipulation.
- Play/manipulation: having overcome the subject’s mistrust, scammers leverage the psychological vulnerabilities that characterise each of us. Thus, by devising credible situations or telling veracious stories, scammers trick victims into divulging critical information about their privacy and security.
- Exit/escape: having achieved their goals, the scammer now covers their tracks. However, they cannot simply “escape” from the online world. In order not to be discovered, the scammer must eliminate everything that could be traced back to them. Therefore, they must hide or destroy their fraudulent means. Scam sites disappear from the Internet, just like fake accounts from social networks. Moreover, in the simplest of cases such as sending an e-mail or a phone call, the attacker only needs to end the scam with a convincing excuse.
Social engineering strategies
Let’s now delve deeper into what Social Engineering is from a psychological standpoint. This is because Social Engineering, in its original form, is a dishonest application of Cialdini’s 6 principles of persuasion: a psychological theory that is usually harmless. It is commonly used in the social sciences and especially in marketing strategies. The psychological vulnerabilities that this theory highlights characterise each of us by our human nature. It is important to recognise them, because they are the basis of any social engineering strategy:
- Reciprocity: we are inclined to ‘return’ a favour, so we are more likely to believe and be helpful to people who give us something.
- Scarcity: we are susceptible to a sense of urgency: we desire what is presented as limited, in short supply, or that could give us access to be a part of an elite. This fear of missing out is abbreviated as “FOMO” in the cryptocurrency market.
- Consistency: we are often unable to or find it very difficult to evade commitments and choices we have made. This is because of psychological the need to show ourselves to be secure and in line with our decisions;
- Authoritativeness: we are prone to interpreting the statements of qualified people as true, because we see them as competent and credible people.
- Consensus: we follow the opinion of the majority, a “social proof” that sees the most common choice as the best one.
- Sympathy: essentially, we are more likely to place our trust in people who look like us or who like us, such as influencers.
Scammers take advantage of these cognitive biases, i.e. mental shortcuts that lead to errors of judgement. They turn them into social engineering strategies. In fact, it is quite easy to ‘fabricate’ a situation that could potentially activate them. For instance, pretending to be a scholar, a famous person or promising non-existent gifts are sufficient prerequisites to manipulate victims. Now, let’s discover the 4 most common social engineering methods in the digital environment. They are therefore also common to cryptocurrencies and blockchain: knowing them is essential to protect yourself from falling for similar situations.
Baiting
Baiting often works through social networks. It consists of presenting false promises of rewards or earnings through these platforms that induce risky actions, such as clicking on misleading links. The situation is often engineered in the following way. It exploits the combination of reciprocity towards those who appear to be giving something away, the scarcity of an offer with limited time and social proof triggered by false claims such as ‘tokens have already been distributed to more than 1,000 people‘. These factors convince users to reveal valuable information (for example the private key of their wallet), duping them into believing it is required to obtain the falsely promised loot. Similar cases can also leverage the authority and sympathy of an account that, although fake, portrays an expert or famous person giving away cryptocurrencies through links placed perhaps in a tweet or a live broadcast.
Scareware
Targets are bombarded with false alarms, through pop-up banners or e-mails, so that they are persuaded to believe that their computer is compromised by a virus or other malware. Scammers exploit the subjects’ fear to convince them to download software, presented as a safe solution. In reality, this is nothing more than malware, transmitted by the scammer themself to steal sensitive information. This case of social engineering might involve collaboration with a hacker to design the hostile software, but this is usually not very complex.
Pretexting
The scammer poses as an authoritative or intimidating figure, such as a law enforcement officer or tax official, to persuade victims to reveal sensitive information in order to resolve fictitious issues. A scammer might also pose as an exchange worker, so as to induce you to reveal your password in order to deal with a fake issue with your account. Remember that no member of the Young Platform team will ever ask you for any password or private key.
Phishing
Phishing is the most widespread method of social engineering and it consists of sending a series of e-mails or text messages. The content of the messages is aimed at creating curiosity, fear or urgency, in order to convince users to click links or download infected attachments. A scammer could also carry out a phishing attempt by making an exact copy of a legitimate website in order to collect access data. The most famous case, in fact, is the ‘password change‘ request for a false intrusion into people’s accounts.. The user enters their old password and a new one in a form that looks the same as the original, but is entirely controlled by the scammer. Thus, the user gives the scammer full access to their exchange wallet, for instance.
In addition to its most common form, phishing can present itself in various ways: through SMS messages or any mobile-supported messaging (Smishing), through fraudulent calls (Vishing), or with specific targets (Spear Phishing), i.e. using strategies created ad hoc for a specific entity (company or individual)
Fact
The CLUSIT 2019 report on security in information and communication technologies (ICT) revealed that, in Italy, 97% of users do not know how to recognise a fake e-mail. So always check that the sender’s address is genuine because, if it isn’t, it could be a phishing attempt.
Now that you know what Social Engineering is, you’ll want to understand how to protect yourself from these psychological manipulations. Especially, avoiding online scams that target your cryptocurrencies is key. It is often said that one can never be too careful and this maxim goes a long way to explaining how to protect oneself against Social Engineering. However, there are other defence tools that are appropriate to protect yourself: let’s look at them together.
How to protect yourself against social engineering
The first strategy to protect yourself against social engineering is to be aware of its existence. The following step is to know the various manipulation techniques they might use against you, to recognise them and to try and prevent them. Reading this article carefully is certainly a good start, but it may not be enough. You need to identify what sensitive information that scammers might try to steal from you. Passwords, seed phrases, private keys, addresses and identities are critical elements in the world of cryptocurrencies, and also in the digital environment in general. So, to understand how to manage and store them, read about password management solutions.
Make sure to periodically review your defence solutions, as social engineering techniques may become more devious and sophisticated over time. Keeping a close eye on the world of crypto may help you avoid falling victim to known cases of social engineering: stay up-to-date with news from the Young Platform blog!