Bitcoin: How does double-spending happen?
February 3, 2022
8 min

Double-spending is the act of making two purchases using the same funds with the clear intention of deceiving a seller of goods or provider of services. This is a problem that any payment system must take into account and avoid when it is designed. How does Bitcoin, whose purchasing power would make double-spending highly profitable, avoid this?
Double-spending: a “genetic” challenge for cryptocurrencies
Double-spending means using the same amount of money in a number of distinct economic exchanges when such expenditure should correspond to a single good or service; it’s the illegal version of a “buy-one-get-one-free” deal at the supermarket.
Although the problem arises in the physical transfer of value, it is not easy to use the same banknote or coin to buy different items (or services): unless you are really lucky, only one of your favourite snacks will come out of the vending machine!
On the other hand, online purchasing using fiat currencies is guaranteed by the issuer of the payment method or by the payment service provider (PSP), which acts as a mediator and guarantor of the legitimacy of the economic transaction, thus reducing the risk of double-spending.
PSP
A Payment Service Provider is a third party entity that allows companies to accept payments through different methods, as it can connect to banks, card issuers and other payment systems. Examples: Google Pay, Apple Pay.
Fraud is a parasite of every economic system, so the world of cryptocurrencies, the new frontier of value, also needs “sanitisation”. Here, however, there are no monopolising third parties; in fact, every transaction occurs on a “peer-to-peer” basis (p2p), directly between seller and buyer, between sender and recipient. In this system, who prevents attempts at double-spending?
The solution is intrinsic to the Bitcoin blockchain, and to show how robust it is, we will analyse the types of attacks with which double-spending could be attempted.
Three attacks, one defence: the Bitcoin blockchain
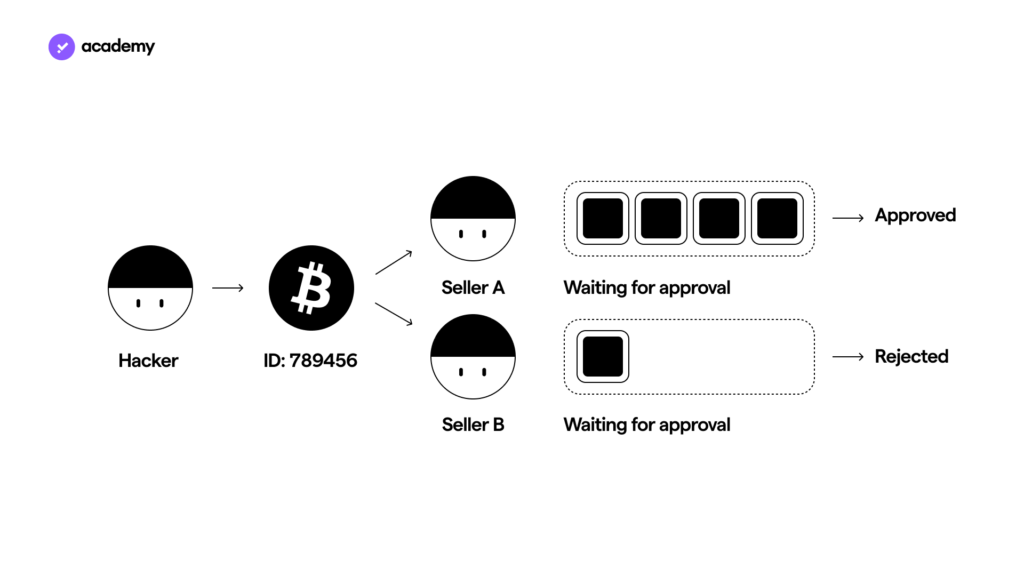
There are several ways to circumvent the Bitcoin system, or other blockchains, to attempt double-spending. In general, by trying to replace the funds’ recipient with the address of a wallet of his own, a hacker could attempt to reacquire the cryptocurrencies, which he had previously just potentially spent.
This could be accomplished in three ways: the Race attack, the 51% attack and the Finney attack. Bitcoin’s blockchain, however, has never failed; it has survived every attack strategy and proven itself with a decade-long defence record. We can tell you about its story in three paragraphs.
The Race Attack: a 10-minute race
To carry out a Race attack, a hacker activates two transactions in quick succession with the aim of using the second one (B) to invalidate the first one (A), where (B) contains information about the transfer of the same funds to a wallet owned by the hacker.
Imagine, for example, that you want to pay at a shop that accepts bitcoin by sending 0.5 BTC, and you use a race attack to send that same 0.5 BTC to your own wallet.
In this situation, double-spending could only be achieved in one way: if A were not registered on the blockchain but overwritten by B, and the shop accepted A, without the latter being confirmed. This is how horse B would win the “race” against A.
Bitcoin, however, protects itself against this contingency: to be certified and thus recorded on the blockchain, all transactions must have the consensus of at least 51% of the network of validator nodes that collaborate in running the blockchain itself.
In the mining article, we have already described how miners ensure blockchain security. In exchange for this contribution, they receive a Bitcoin reward for each block created, which is algorithmically halved every four years in the “Halving” process. Competition is therefore very high, and as the power of the mining devices increases, so does the difficulty of the cryptographic problems to be solved; this stabilises the block production rate (one every 10 minutes) and increases the security of the blockchain.
How does this complex validation system prevent a certain number of bitcoins from being spent twice? Before the seller releases the good or service, it would suffice to wait for A’s information to be confirmed by the nodes.
51% attack vs Hash Rate
The same applies to the 51% attack: to spend a Bitcoin, or a fraction of it, twice, a hacker would have to “rewrite” each block created after the transaction they are trying to tamper with. In fact, each block is linked to the previous and the next by means of the hash function, so that to modify even one transaction within it would have to alter the information of all subsequent blocks, with a chain effect. The blocks are like a line of children holding hands with their friends: you can’t break the order without a fight!
The only way to attempt such a change would be to perform a 51% attack, which, as the name suggests, would require control of at least half “plus one” of the network’s computing power (Hash Rate). Only in this way could hackers manipulate a block to duplicate its transactions. This is, however, an impossible undertaking, as well as being thoroughly unprofitable in terms of the hardware and energy costs. No one has ever succeeded, and I would definitely not recommend trying this at home.
Finney attack vs PoW
What happens if a miner attempts a double-spending attack?
In a Finney attack, a miner uses a block to pre-record the movement of a certain amount of A coins in his possession from one of his wallets to another while waiting for the validation of a block for the Bitcoin blockchain.
A miner becomes eligible to verify a block by means of the “Proof-of-work” consensus algorithm. Thus, in order to carry out a Finney attack, at the moment when the algorithm grants the miner precedence over other nodes, it does not forward the pre-mined block but sends the same A cryptocurrencies to a seller and waits for the corresponding good or service to be rendered.
When it receives what has been requested, and before that transaction is confirmed, the miner transmits the pre-mined block so as to superimpose the first transfer (to the seller) with the second one (to an address of its own).
Why is this unlikely, if not impossible, in the Bitcoin blockchain?
A miner, especially a small one, is rarely chosen by the PoW due to the low Hash Rate it can sustain.
Furthermore, even if that particular miner is chosen, in the time it takes for the seller to accept the transaction, it is likely that a valid block will be found more quickly, which would then render the one containing the fraudulent transaction invalid.
Thus, the seller, as with the race attack, would only need to wait for confirmation from the network that it has received the cryptocurrencies, before releasing the good/service, so as to record this transaction immutably in a blockchain.
In addition, the miner would lose the reward of the block on which it had priority, as it would not be able to transmit it “in time” (within the 10 minutes): at that moment, and until the next Halving, it would amount to 6.5 BTC, a rather significant amount.
Fun fact
The Finney Attack is named after Hal Finney, the first to have acknowledged the phenomenon in the Bitcointalk forum as well as being the first to receive a Bitcoin from Satoshi Nakamoto himself! Such an event is comparable to handing over the Ten Commandments; would you be ready to pass on the Word of Bitcoin?
Are my Bitcoins safe?
Bitcoin reduces the problem of double-spending to a hypothetical threat, provided that the sellers exploited for such a fraudulent attempt only accept secure transactions (i.e. confirmed by the blockchain).
So, in short: yes, your bitcoins are safe from double-spending. In fact, the Digital Gold protocol was reinforced with several protective mechanisms at the design stage. These include:
- the fixed rate of issue of coins (1 block every 10 minutes)
- the Proof-of-work (PoW) consensus algorithm
- a reward mechanism that incentivises miners to increase their computing power while keeping the difficulty of their work high enough to secure the entire network.


